Securing SaaS with Australia's Essential Eight: Best Practices for Cyber Resilience
Join hundreds of companies and start your identity governance journey today
How many SaaS apps does your company use? Ten? Fifty? More? Most IT teams don’t have a clear answer. Employees sign up for tools without approval, admin privileges pile up, and before you know it, your company is running dozens—maybe hundreds—of untracked shadow apps. Every one of them is a potential security risk such as data breaches, malware infections, and account hijacking.
That’s why Australia’s Essential Eight exists. Developed by the Australian Cyber Security Centre (ACSC), this cybersecurity framework helps businesses protect their systems from cyber threats, particularly those that could lead to significant financial or reputational damage. However, the rise of cloud-based SaaS applications presents new security challenges. Companies now struggle with Shadow IT, weak access controls, and compliance gaps.
While the Essential Eight is applicable to all environments, including SaaS, organisations need to adapt their implementation approach to address the unique characteristics of cloud-based applications. This document explores how the Essential Eight can be applied to secure SaaS apps and provides practical guidance for organisations looking to enhance their SaaS security posture.
Mapping SaaS Management to the Essential Eight
A) Application Control with a SaaS Management Platform
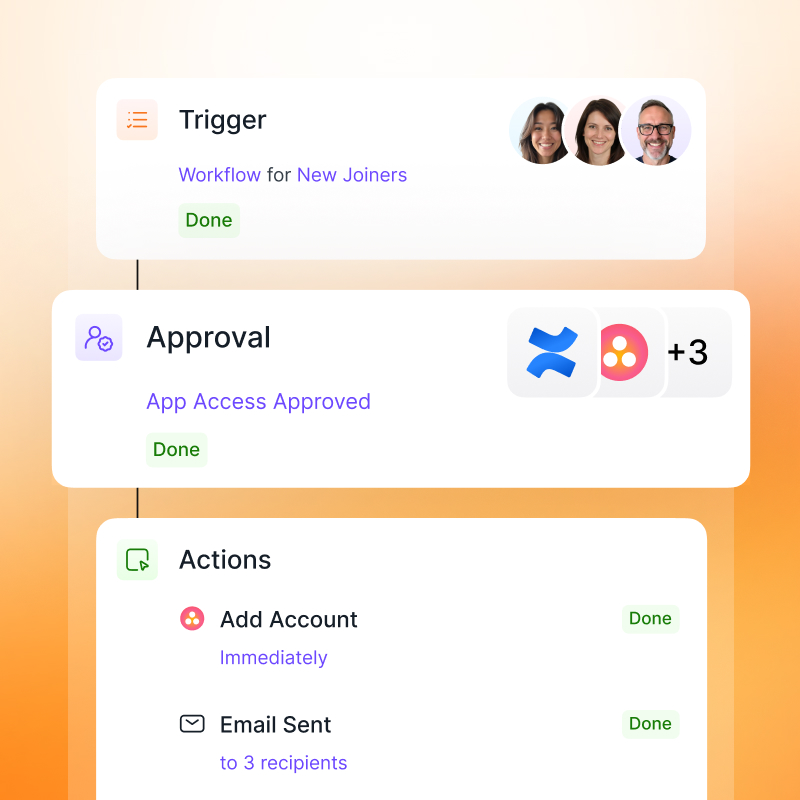
Businesses often lose track of their SaaS applications. Employees sign up for tools on their own, leaving IT teams unaware of what’s running in the background. This creates Shadow IT, where unapproved applications are in use outside of approved security policies, increasing the risk of data leaks and compliance violations.
To meet Essential Eight requirements, organisations must monitor and control SaaS applications. This means identifying unauthorised tools, enforcing security policies, and ensuring only approved applications are in use. Without visibility, businesses risk exposure to unpatched vulnerabilities, weak authentication settings, and data governance failures. Strong application control is essential to reduce these risks.
B) How Josys Helps Restrict Administrative Privileges
Too many admin accounts create unnecessary security risks. The more people with high-level access, the easier it is for cybercriminals to exploit credentials and gain control of critical systems. Essential Eight recommends tight restrictions on admin privileges to limit exposure.
Josys helps IT teams identify and manage admin accounts across SaaS applications. It flags super-admin and admin privileges, ensures role-based access control (RBAC) is enforced, and automates periodic reviews to prevent privilege creep. Compliance reports provide a clear record of access controls, making audits easier. By minimising unnecessary privileges, businesses reduce the risk of insider threats and account takeovers.
C) Leverage Josys to Monitor Multi-Factor Authentication (MFA)
MFA is one of the most effective ways to prevent unauthorised access, but many companies fail to enforce it across all SaaS applications. The Essential Eight strongly recommends implementing MFA across user accounts to minimise security risks, but many organisations struggle with inconsistent policies or lack visibility into which users are properly protected.
Josys provides real-time MFA monitoring, identifying accounts that lack proper authentication. IT teams receive instant alerts if a privileged access user hasn’t enabled MFA, allowing them to take immediate action.. This eliminates security blind spots and strengthens access control across all SaaS applications.
D) Proactive Threat Detection & Response
Cyber threats evolve quickly, and businesses need real-time monitoring to catch suspicious activity before it leads to a breach. Essential Eight encourages proactive threat detection, focusing on identifying unauthorised access attempts, privilege escalations, and system misconfigurations.
Organisations must have continuous security monitoring in place to detect anomalies across their SaaS environment. This includes tracking login patterns, monitoring privilege changes, and integrating with security event management platforms to respond faster to potential threats. By staying proactive, businesses can reduce response times and prevent security incidents before they escalate.
Best Practices for SaaS Security Compliance
SaaS security isn’t a one-time task—it requires continuous monitoring and automation. Essential Eight compliance is easier when IT teams have real-time security dashboards to track risk levels and enforce policies. Regular SaaS audits ensure that applications remain compliant and no unauthorised tools slip through.
Instead of relying on manual enforcement, companies should implement automated security workflows that apply Essential Eight policies consistently. Employee security training is also key. Staff need to understand secure SaaS usage, phishing risks, and proper password management to help maintain a strong security posture.
Conclusion
Managing SaaS security is tough, but ignoring it isn’t an option. Essential Eight provides a clear security framework, but manual enforcement can be overwhelming. Josys simplifies SaaS security, automating compliance, enforcing policies, and giving IT teams full control over their cloud applications.
With automated security controls, access governance, and compliance tracking, Josys helps businesses reduce cyber risks and meet Essential Eight standards—without the manual workload.
Want to see how it works? Schedule a demo today and take control of your SaaS security.
over your identities, applications, and files?
Sign-up for a 14-day free trial and transform your IT operations.