The Evolution of Shadow IT Management
Join hundreds of companies and start your identity governance journey today
.avif)
While shadow IT allows employees to use tools they like, it brings about security risks like data breaches and cyber-attacks. Also, since there's no proper oversight of these unauthorized apps and devices, ensuring their compliance with established standards and regulations becomes difficult, which could land the organization in trouble.
Shadow IT can cause more harm than good for an organization's IT setup, so it's important to manage it well to prevent resource wastage, exposure to security risks, and compliance and efficiency issues.
The Traditional Method of Managing Shadow IT
While the standard method of managing Shadow IT offers organizations basic control, its heavy reliance on manual methods, limited scalability and reactive approach make it less effective in today's fast and complex digital world. Its basic features and limitations include:
- Manual and ad-hoc identification.
- Unreliable and time-consuming identification of security risks.
- Verifying adherence to IT policies relies on trusting employees and inconsistent checks, leading to compliance risks.
- A reactive approach to addressing Shadow IT issues rather than preventing them makes it difficult to mitigate potential risks.
- Limited scalability and adaptability hinder innovation and flexibility as organizations grow.
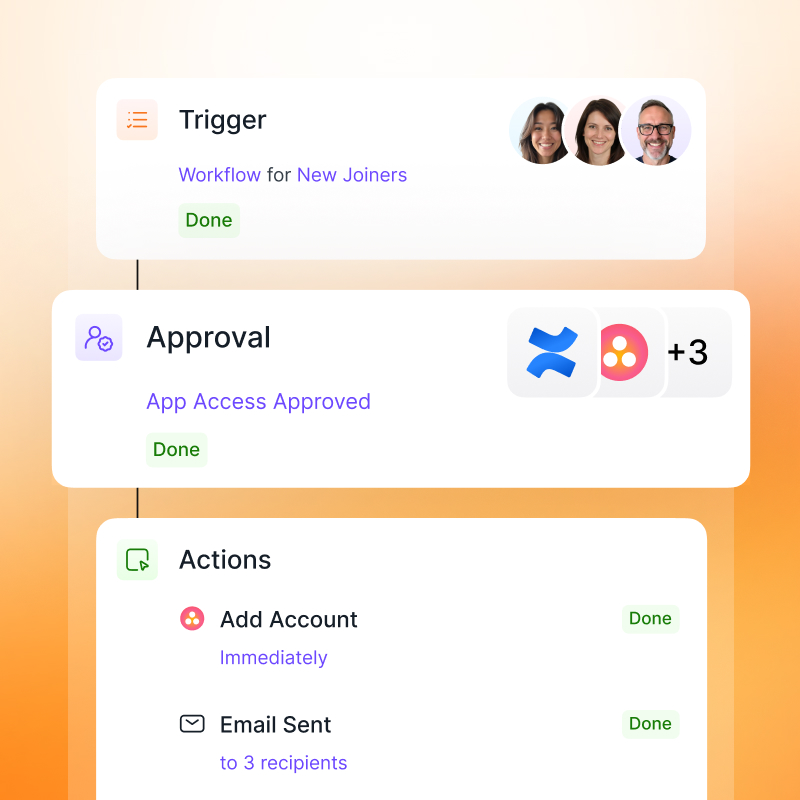
Josys: A Modern Approach to Shadow IT Management
As a comprehensive SaaS and Device Management Platform, Josys redefines efficiency, security, and control for IT departments overwhelmed by the challenges of employees using unauthorized applications. Let's delve deeper into Josys' approach to shadow IT management:
- Detection and Identification: Josys uses its 240+ app integrations, browser extension, and Google audit logs to discover any unmanaged, or unknown shadow IT apps being used. This allows IT to take control and take action against high-risk apps or integrate them into the managed applications.
- Risk Assessment and Mitigation: Josys provides detailed application security certifications for each app for informed decision-making, smarter risk assessment, and proactive mitigation.
- Shadow Account Identification: If SaaS management is decentralized, IT teams can lose track of user access permissions. Josys surfaces accounts that are accessing company-managed apps that are not in your active directory, ensuring only proper users are accessing company data.
- Scalability and Adaptability: Josys provides a solution that is both scalable and adaptable to organizations of all sizes, ensuring efficient, secure, and compliant Shadow IT management.
Why Josys is the Superior Choice
Josys stands out as a top choice for shadow IT management, providing a proactive and adaptable solution that overcomes the shortcomings of traditional methods. Josys features that make it a better choice:
- Automated processes for enhanced efficiency and accuracy.
- Comprehensive information and risk assessments for proactive risk mitigation.
- Confirmation of compliance with IT policies, reducing compliance gaps and penalties.
- Minimizes the impact of Shadow IT on business operations and security.
- Scalable and adaptable solution that ensures effective Shadow IT management as the organization grows.
Conclusion
Since standard IT management methods are outdated and inefficient, there's a need for a more effective approach. Josys emerges a modern automated solution that's proactive, thorough, and adaptable, overcoming the limitations of standard methods.
For IT managers and decision-makers looking to transform their approach to Shadow IT and harness the full potential of their IT assets, Josys offers a compelling solution. Schedule a demo today to discover how Josys can help you effectively manage shadow IT, ensure security and compliance and improve your overall IT ecosystem.
over your identities, applications, and files?
Sign-up for a 14-day free trial and transform your IT operations.