What is an Access Policy?
Join hundreds of companies and start your identity governance journey today

For IT directors, managing who gets access to what resources can quickly become a maze of permissions, roles, and exceptions. When your organization uses dozens of SaaS applications and hundreds of devices, maintaining security while keeping operations flowing smoothly feels like walking a tightrope. This balancing act is where access policies become indispensable, ensuring organizations save on time and cost while boosting visibility by streamlining access management and reducing cybersecurity risks.
What is an Access Policy?
An access policy is a set of rules that defines which users can access specific resources, under what conditions, and what actions they can perform once access is granted. Think of it as a comprehensive blueprint that governs how your organization's digital assets are accessed and used.
Access policies formalize security decisions, removing ambiguity and ensuring consistent application of security principles across your organization. Instead of making one-off decisions for each access request, well-defined access management policies create a framework that can be applied autonomously.
How Access Policies Work
Access policies operate on several key principles that work together to create a cohesive security framework:
1. Identity Verification
Before granting access, the system must verify who is requesting it. This typically involves authentication through:
- Username and password combinations
- Multi-factor authentication (MFA)
- Biometric verification
- Single sign-on (SSO) systems
2. Authorization Rules
Once identity is confirmed, authorization determines what the user can access based on:
- Role-based access control (RBAC)
- Attribute-based access control (ABAC)
- Time-based restrictions
- Location-based restrictions
3. Least Privilege Principle
Users should only have access to the resources necessary for their job functions—nothing more. This minimizes potential damage from compromised accounts or insider threats.
4. Conditional Access
Modern access policies often include contextual factors such as:
- Device compliance
- Network location
- Time of day
- Behavioral patterns
5. Monitoring and Enforcement
Effective policies include continuous monitoring to:
- Track access attempts
- Log user activities
- Identify unusual behaviors
- Enforce policy violations automatically
How the Josys Platform Tackles Access Policies
"Access policies create exponential freedom. Invest tens of minutes in Josys and free up tens of hours every month, ongoing," explains Tim Silva, Product Lead at Josys. "Our AI-powered identity management suggestions offer you highly accurate, audit-ready policies based on smart patterns detected across user profiles. It understands that everyone in engineering needs access to GitHub and Jira. Use modern IT and free yourself to concentrate on higher-value tasks."
The Josys platform approaches access policies through several integrated capabilities:
- Centralized Policy Management: Get a bird's-eye view of all your access policies in one unified dashboard.
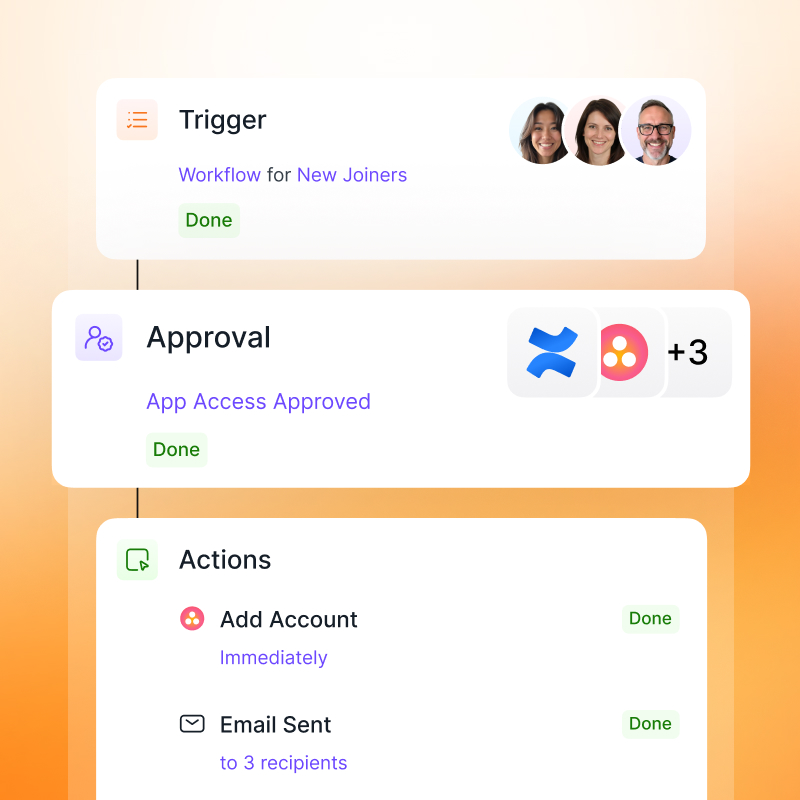
- Automated Workflows: Create standardized processes for common scenarios like onboarding, role changes, and offboarding.
- Role-Based Templates: Deploy pre-configured access groups based on department, seniority, or project needs.
- Real-Time Visibility: Monitor access patterns across your organization with comprehensive reporting.
- Compliance Support: Maintain audit trails and documentation to support regulatory requirements.
Security Without Friction
Effective access policies strike the perfect balance between security and usability. When implemented thoughtfully, they protect your organization's most valuable assets while enabling your team to work efficiently.
The right access policy framework evolves with your organization, adapting to new applications, emerging threats, and shifting business requirements. By centralizing these policies in a platform like Josys, IT directors can transform access management from a constant headache into a strategic advantage. Book a demo to learn more.
over your identities, applications, and files?
Sign-up for a 14-day free trial and transform your IT operations.